5-Nine Cloud Security is a security solution for Microsoft Cloud OS and Hyper-V. This solution provides an firewall, an antivirus and an IDS (Intrusion Detection System) to detect malicious attacks. Cloud Security can secure a multi-tenant Hyper-V environment to protect each tenant VMs and hypervisor. Moreover the Hyper-V hosts are protected with agentless antivirus. 5-Nine Cloud Security can be integrated into the Windows Azure Pack to provide Security as a Service.
In this topic, I will implement the 5-Nine Cloud Security in a Windows Azure Pack environment. This topic is the first of a series.
- Part 1: Implement 5-Nine Cloud Security 5.1
- Part 2: Configure 5-Nine Cloud Security for Windows Azure Pack
- Part 3: Protect tenant VMs
5-Nine Cloud Security 5.1 overview
5-Nine Cloud Security is composed of 5 features that have to be deployed on specific servers:
- Management Service: this feature should be deployed on a dedicated VM. This is the management server of the solution;
- Management Console: this feature enables to configure and manage the 5-Nine Cloud Security solution. This feature should be installed on the Management Service server and on console servers;
- Host Management Service: this component should be installed on Hyper-V hosts to have the visibility on Virtual Machines
- SC VMM compliance extension: this component should be installed on Virtual Machine Manager servers. Thanks to this feature, a configuration provider is added to Virtual Machine Manager. This enables to add a Cloud Security Network Service and extensions to logical switch.
- Extension for Windows Azure Pack: This feature should be installed on Windows Azure Pack servers. This enables to add 5-Nine Cloud Security tab on admin and tenant portals to make the configuration.
Below you can find a schema of the deployment that I have made in my lab.

You can download and request a trial license key of 5-Nine Cloud Security 5.1 here. For this topic, I have downloaded the Standalone with Kaspersky Antivirus version.
Management Service and Management Console installation
First, I have deployed a new virtual machine called vmsec01. On this server I have run 5nineCloudSecurityKAV.exe. Next I select Management Service and I have clicked on Install.
Next click on next many times and choose a destination folder.
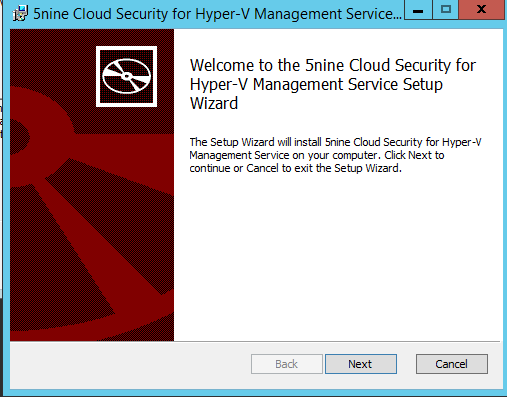
Specify a domain service account and click on next.
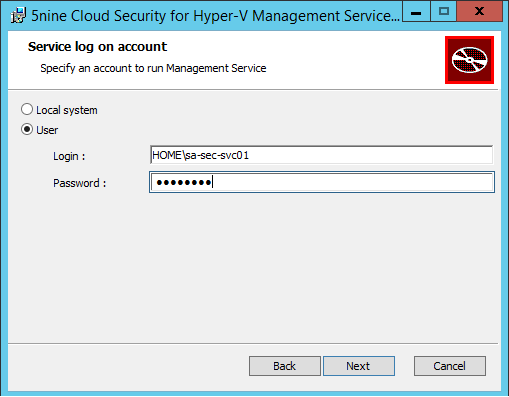
Next specify a database server and credential. I have specified a SQL Server AlwaysOn endpoint based on SQL Server 2012 SP1.
When the installation is finished, you can select the Management Console and click on install.
Next I choose a destination folder and I click on next.
Then specify the management server address. Because I install the management console on the same server where is the management server, I specify localhost. If you install the management console on another server, you have to specify the FQDN of the management server.
When the management console is installed, you can open the console. You should have something like this.
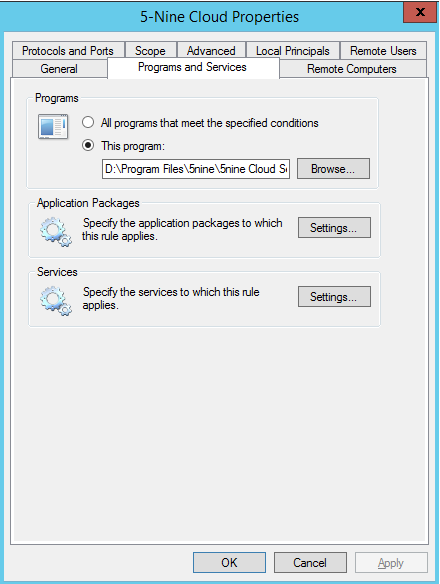
To finish, I recommend you to create a firewall exception based on this program: D:\<InstallPath>\5nine\5nine Cloud Security for Hyper-V Management Service\5nine.VirtualFirewall.ManagementService.exe
Host Management Service installation
Local installation
Connect to a Hyper-V host and run 5nineCloudSecurityKAV.exe. Select Host Management Service and click on Install.
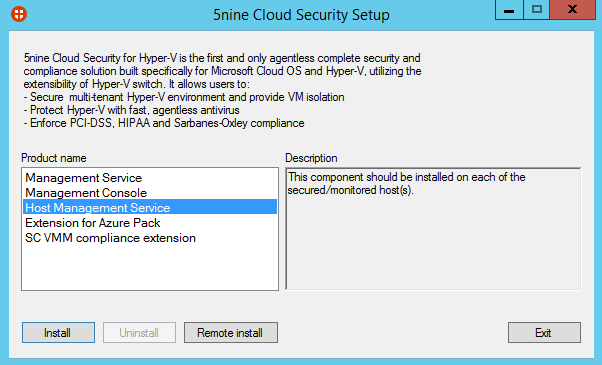
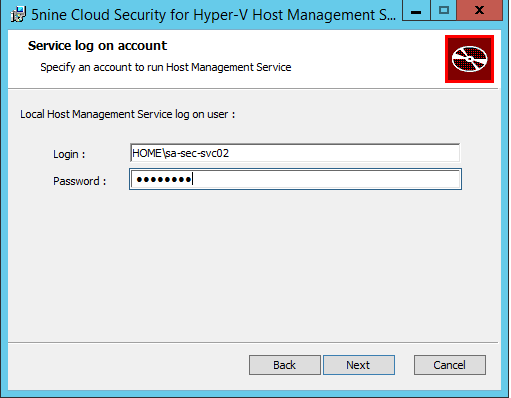
Click on next, choose a destination folder and specify a service account for the Host Management Service.
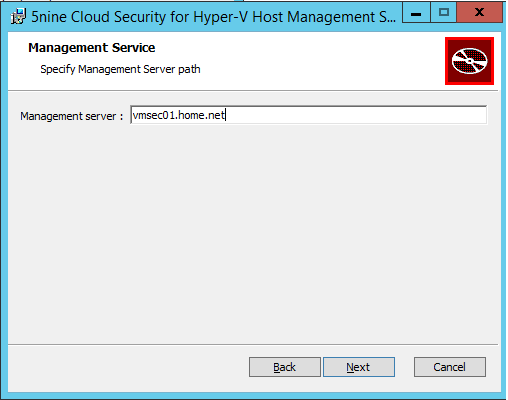
Then specify the management server FQDN.
Remote installation
You can also install the Host Management Service remotely. For that, run 5nineCloudSecurityKAV.exe, select Host Management Service and click on Remote Install.
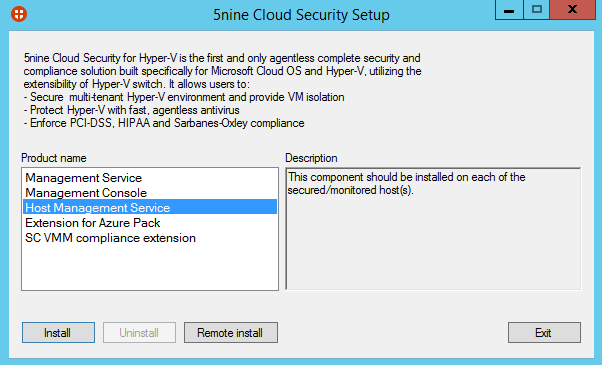
Next specify the management server FQDN.
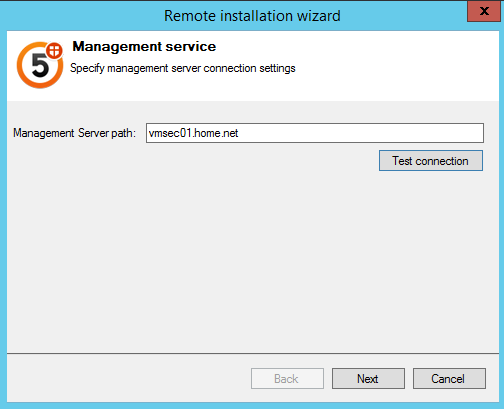
Next add each Hyper-V hosts where you want to install the service and the service account.
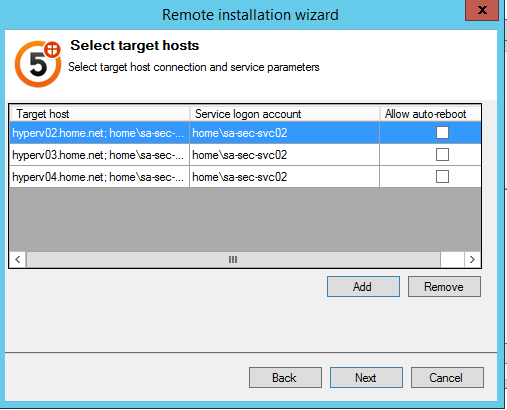
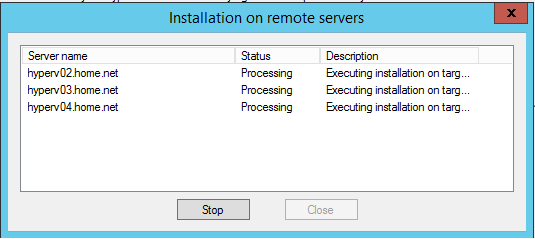
Click on next and the installation should be launched on each Hyper-V.
Virtual Machine Manager extension
Install SC VMM Compliance extension
Connect on each Virtual Machine Manager server and run 5nineCloudSecurityKAV.exe. Select SC VMM compliance extension and click on next.
Select a destination folder and click on next.
Once you have finished to install this feature, reboot the Virtual Machine Manager service.
Configure Virtual Machine Manager
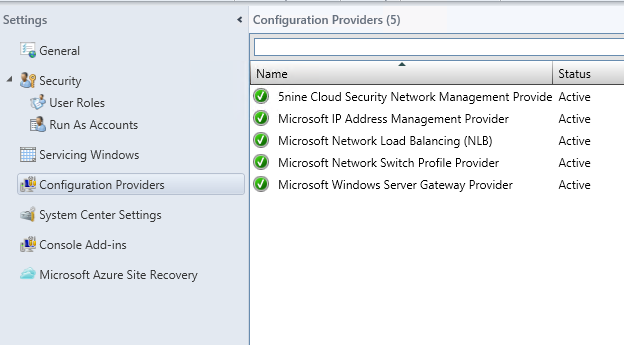
Connect to your Virtual Machine Manager and navigate to settings. Click on Configuration Providers and verify that 5-nine Cloud Security Network Management Provider is active.
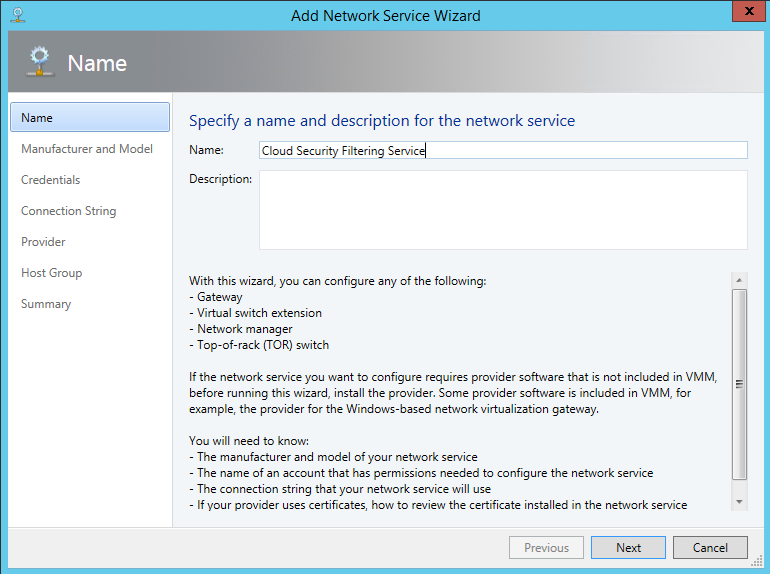
Next navigate to the fabric and add a network service. Give a name to the network service and click on next.
Select 5nine Software, Inc as Manufacturer and CloudSecurity Manager as Model.
Specify a RunAs account. I have created a RunAs account called CloudSecurity based on management server service account credential.
Then specify the Management Server FQDN and click on next.
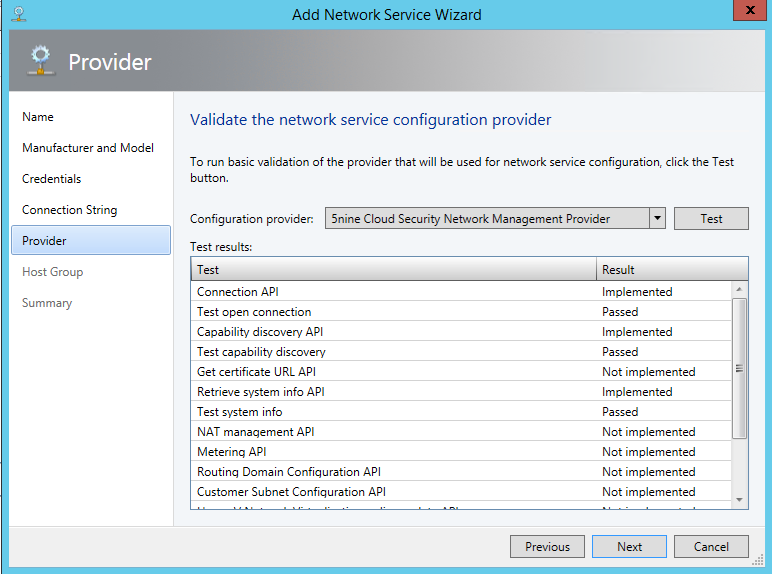
Next validate the network service configuration provider by clicking on Test and if the test result is good, click on next.
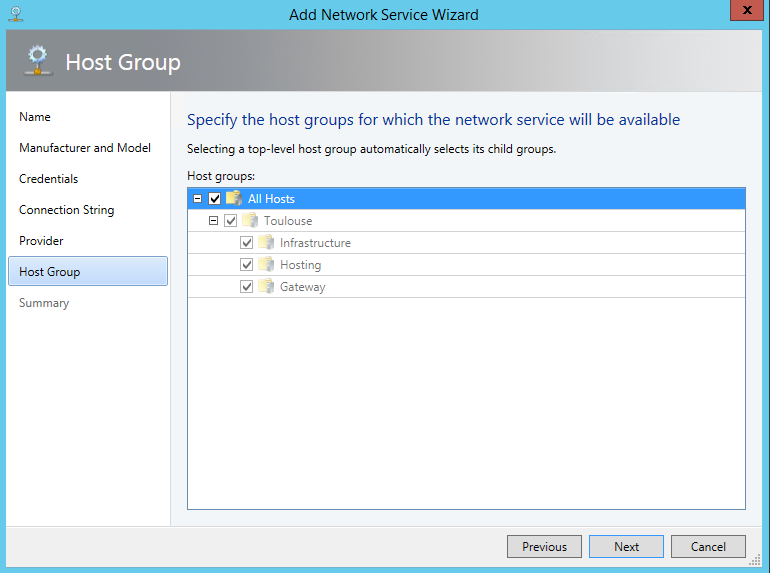
Select the host groups where the network service will be available.
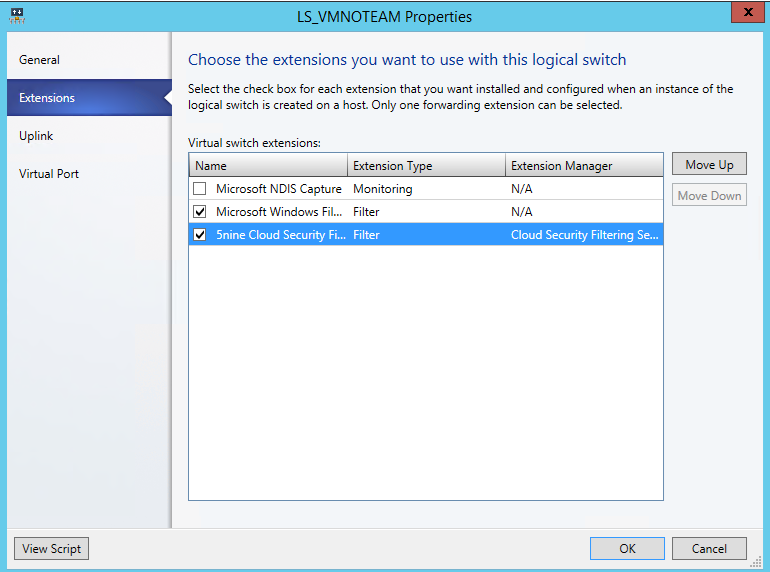
To finish, edit each logical switch and select 5nine Cloud Security Filter extension.
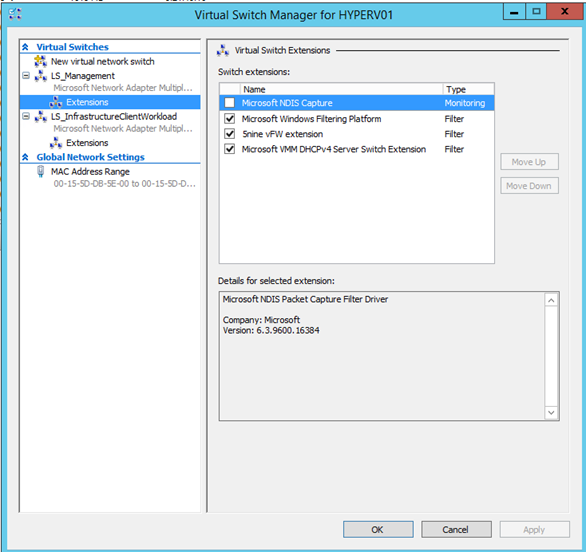
Now connect to Hyper-V Manager and verify if extensions are in the same order as VMM configuration:
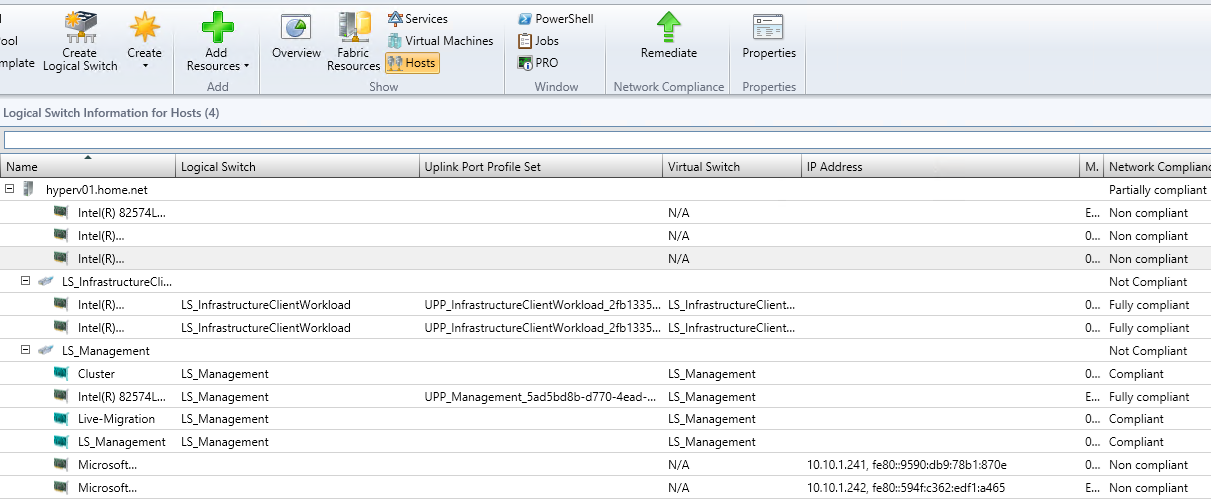
To finish verifying if the related interface are compliances as below:
Windows Azure Pack extension installation
Now connect to your Windows Azure Pack servers and run 5nineCloudSecurityKAV.exe. Select Extension for Azure Pack and click on install.
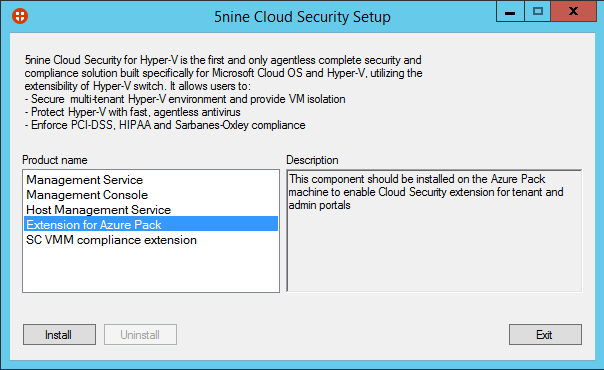
Select the features to install regarding the Windows Azure Pack server roles.
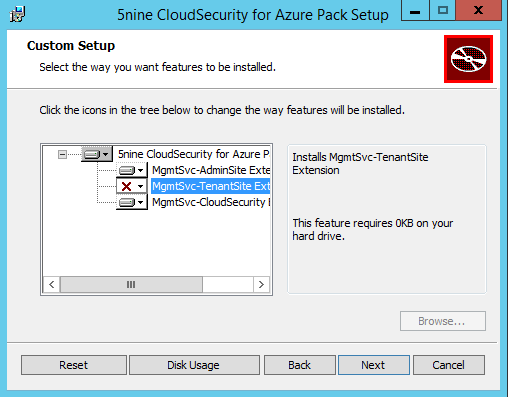
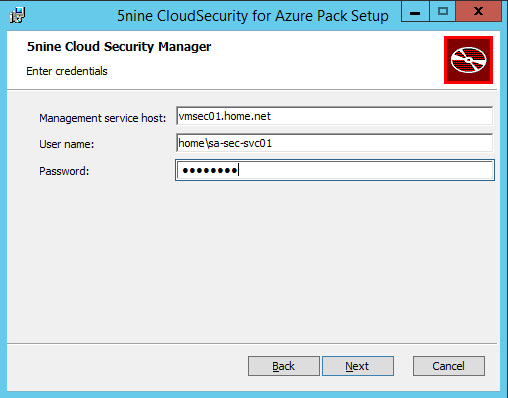
Next specify the hostname and the credentials to connect to Management Server.
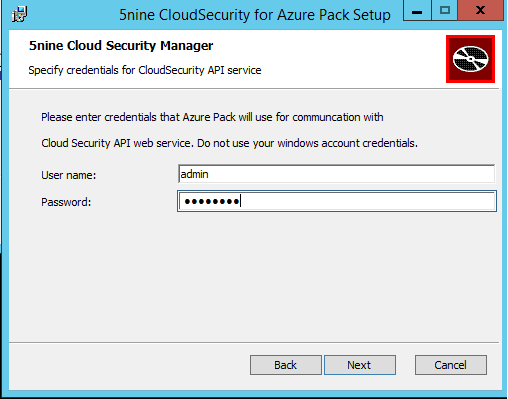
Next specify credentials for communication between the Windows Azure Pack and Cloud Security API web service.
Once you have finished installation of Windows Azure Pack extension, you should have a new tab in the Admin Portal.
In this next part, I will explain you how to configure 5-Nine Cloud Security in Windows Azure Pack.






