- Public Key Infrastructure Part 1 – introduction to encryption and signature
- Public Key Infrastructure Part 2 – main components
- Public Key Infrastructure Part 3 – implement a PKI with Active Directory Certificate Services
- Public Key Infrastructure Part 4 – Configure CRL
- Public Key Infrastructure Part 5 – Registry key, certutil and Active Directory
- Public Key Infrastructure Part 6 – Manage certificate templates
- Public Key Infrastructure Part 7 – Enrollment and Auto-enrollment
- Public Key Infrastructure Part 8 – OCSP responder
- Public Key Infrastructure Part 9 – Management accounts
- Public Key Infrastructure Part 10 – Best practices about PKI
In this part I will talk about management accounts regarding:
- CA management: To manage CA we will implement Role-Based Administration;
- Recovery Agent: account which is able to recover all private keys.
These CA management accounts are important to increase the security level of your PKI. PKI is a security component and should be managed by security officers. But it is not always the same security officer who manages CAs, certificates or audit logs. Moreover, the CAs backups are usually managed by the backup team and Windows server is managed by the system admin. So it is necessary to implement Role-Based Administration.
Regarding Recovery Agent, it is a special account that is able to recover all private keys. This is why this agent should be associated with a security officer account. If this account is corrupted, all data of your company could be decrypted …
Role-Based Administration
Permission description
All tables on this part are taken from TechNet.
I have copied tables from TechNet because they explain very well the different permissions. Four permissions are managed from Certificate Services: Manage CA, Issue and Manage Certificates, Read and Enroll. Backup Operator and Auditor roles are managed from the operating system.
|
Roles and groups |
Security permission |
Description |
|
CA administrator |
Manage CA |
Configure and maintain the CA. This is a CA role and includes the ability to assign all other CA roles and renew the CA certificate. These permissions are assigned by using the Certification Authority snap-in. |
|
Certificate manager |
Issue and Manage Certificates |
Approve certificate enrollment and revocation requests. This is a CA role. This role is sometimes referred to as CA officer. These permissions are assigned by using the Certification Authority snap-in. |
|
Backup operator |
Back up file and directories Restore file and directories |
Perform system backup and recovery. Backup is an operating system feature. |
|
Auditor |
Manage auditing and security log |
Configure, view, and maintain audit logs. Auditing is an operating system feature. Auditor is an operating system role. |
|
Enrollees |
Read Enroll |
Enrollees are clients who are authorized to request certificates from a CA. This is not a CA role. |
In the below table, you have the Activity related to the role of the user.
| Activity |
CA administrator |
Certificate manager |
Auditor |
Backup operator |
Local administrator |
Notes |
| Install CAs |
|
|
|
|
X |
|
| Configure policy and exit modules |
X |
|
|
|
|
|
| Stop and start the Active Directory Certificate Services (AD CS) service |
X |
|
|
|
|
|
| Configure extensions |
X |
|
|
|
|
|
| Configure roles |
X |
|
|
|
|
|
| Renew CA keys |
|
|
|
|
X |
|
| Define key recovery agents |
X |
|
|
|
|
|
| Configure certificate manager restrictions |
X |
|
|
|
|
|
| Delete a single row in the CA database |
X |
|
|
|
|
|
| Delete multiple rows in the CA database (bulk deletion) |
X |
X |
|
|
|
The user must be both a CA administrator and a certificate manager. This activity cannot be performed when role separation is enforced. |
| Enable role separation |
|
|
|
|
X |
|
| Issue and approve certificates |
|
X |
|
|
|
|
| Deny certificates |
|
X |
|
|
|
|
| Revoke certificates |
|
X |
|
|
|
|
| Reactivate certificates that are placed on hold |
|
X |
|
|
|
|
| Renew certificates |
|
X |
|
|
|
|
| Enable, publish, or configure certificate revocation list (CRL) schedules |
X |
|
|
|
|
|
| Recover archived keys |
|
X |
|
|
|
Only a certificate manager can retrieve the encrypted key data structure from the CA database. The private key of a valid key recovery agent is required to decrypt the key data structure and generate a PKCS #12 file. |
| Configure audit parameters |
|
|
X |
|
|
By default, the local administrator holds the system audit user right. |
| Audit logs |
|
|
X |
|
|
By default, the local administrator holds the system audit user right. |
| Back up the system |
|
|
|
X |
|
By default, the local administrator holds the system backup user right. |
| Restore the system |
|
|
|
X |
|
By default, the local administrator holds the system backup user right. |
| Read the CA database |
X |
X |
X |
X |
|
By default, the local administrator holds the system audit and system backup user rights. |
| Read CA configuration information |
X |
X |
X |
X |
|
By default, the local administrator holds the system audit and system backup user rights. |
Modify CA management accounts
Now I’m going to show you how to implement Role-Based Administration in practice. For that, I have created some groups in Active Directory:
- GA-CAAdmins: Manage CA.
- GG-CertificateMgmt: Manage Certificates
- GG-SecurityLogMgmt: permissions on security event logs.

To manage permissions for Certificate Services, open a certification authority console and right click on CA name. Select properties. Navigate to Security tab. First I have deleted permissions for Domain Admins group. Next I have added the group GG-CAAdmins with below permissions:
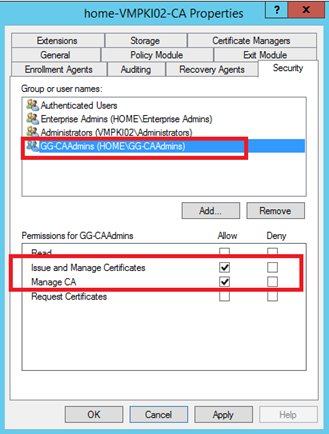
After that, I have added GG-CertificateMgmt group as below:
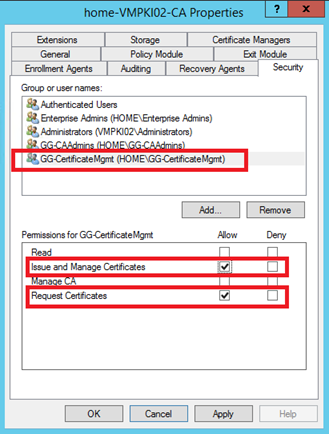
On Certificate Services side, I have finished. Now I want to set permissions on security logs auditing. For that open gpedit.msc (you can make the same thing by GPO). Navigate to Computer Configuration, Windows Settings, Security Settings, Local Policies and User Right Assignments.
Edit Manage auditing and security log policy and add the related group. On my side I have added GG-SecurityLogMgmt.
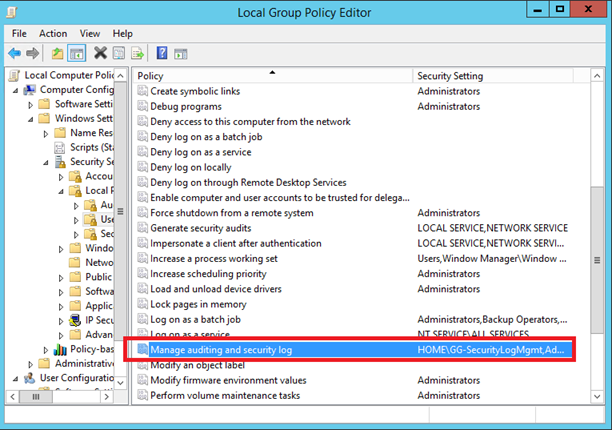
To finish, add to Backup Operators (from Active Directory or local group) accounts that need backup permissions.
Recovery Agent
Now I would like to spend some time about Recovery Agent. This feature is very important if you encrypt corporate data. Depending on your country and your law, security officers must be able to unencrypt information for a while even if the employee has left. To be able to unencrypt all data even if the private key of the user has been lost, you should use recovery agent.
The principle is simple: all private keys generated by client are copied in a key archival. Then the recovery agent certificate is able to open this key archival. To recover data, just extract the related private key from key archival and use it to unencrypt data.
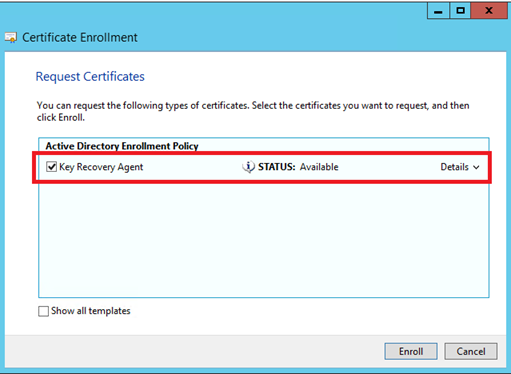
To implement Key Archival, I will create a certificate for Romain Serre using Key Recovery Agent certificate template:
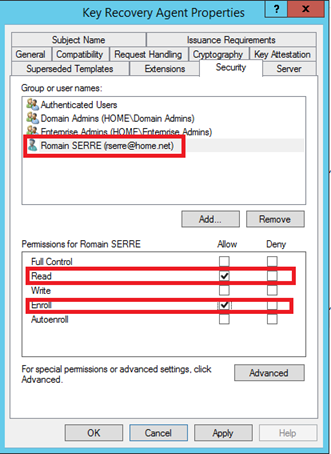
In security tab, I add my account with Read and Enroll permissions.
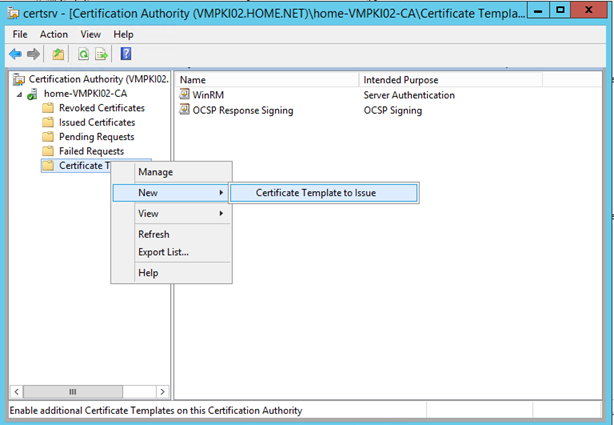
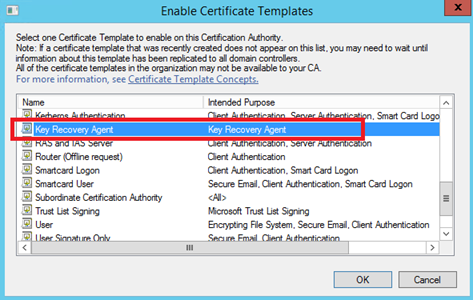
Next I configure my CA to issue the certificate template:
Now I open a mmc with certificates snap-ins which manage my user account:
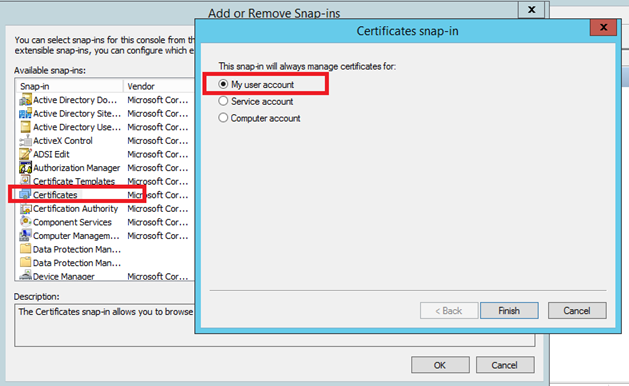
Right click on Personal and select All tasks, Request New Certificate.
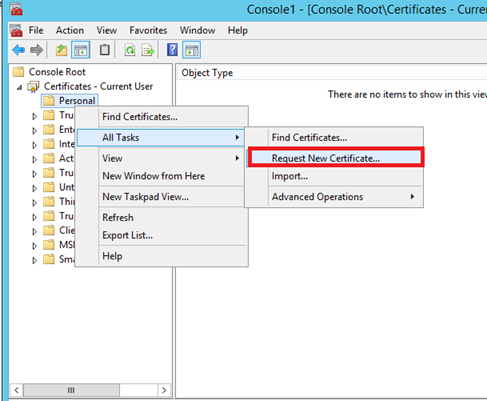
When you are asked for a certificate template, select Key Recovery Agent and click on Enroll. At the end of this process, the enrollment is pending and wait for your approval.
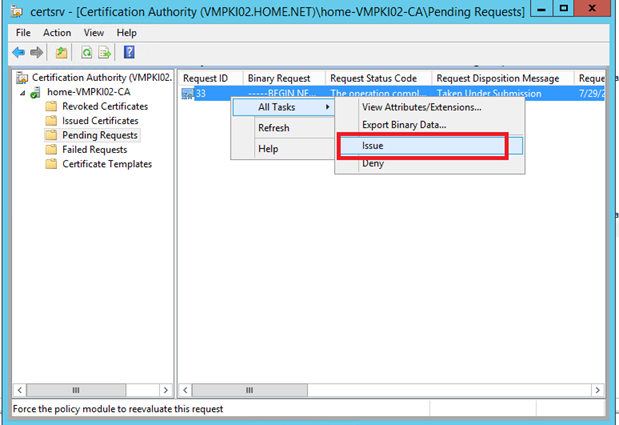
To approve the certificate request, open the certification authority console and click on Pending Requests. Right click on your certificate and select All Tasks and Issue.
Now open issued certificates and double click on the previously issued certificate. Navigate to the Details tab and export the certificate by clicking on Copy to file. Follow the process and export your certificate to .cer file.
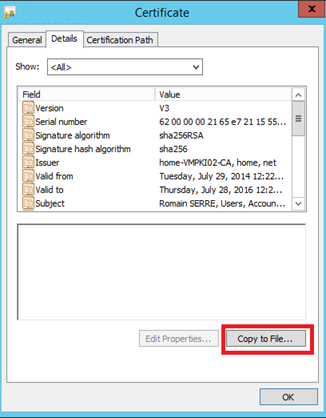
Once your certificate is exported, go back to your mmc and right click on Personal. Select All Tasks and import as below.
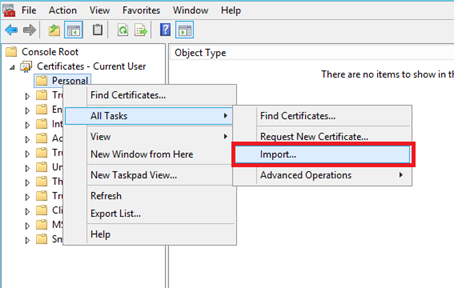
Follow the import process and select the .cer file that you have just exported. Now you should have the certificate in your personal store.
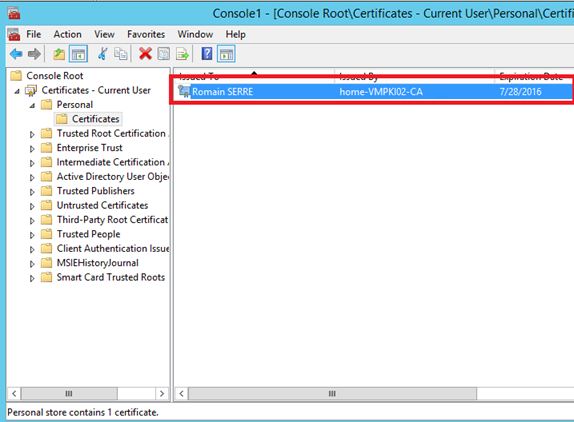
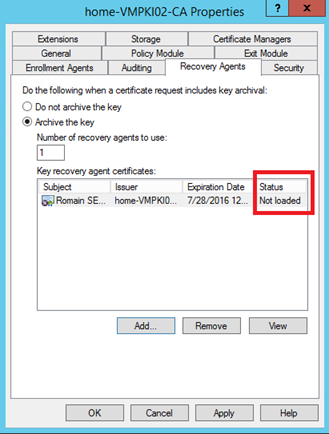
To configure the Key Archival, open the certification authority, right click on the CA name and select properties. Navigate to Recovery Agents tab. Select Archive the key, click on Add and select the certificate:
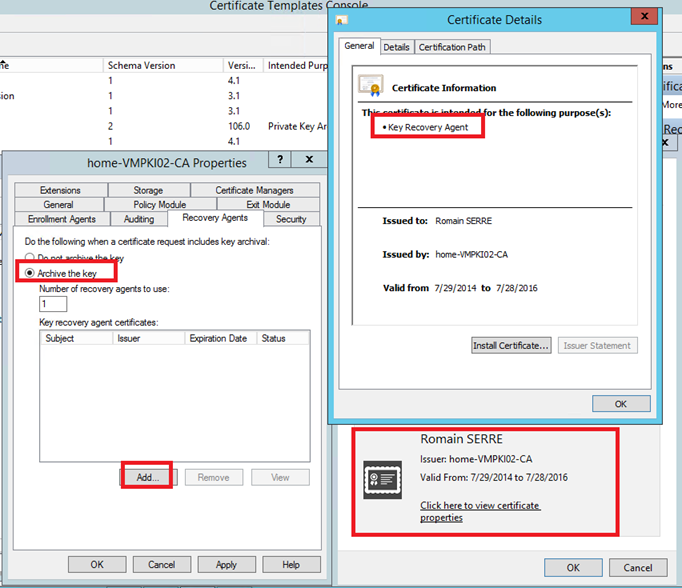
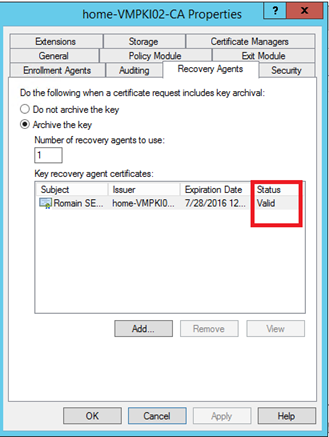
Before restarting Certificate Services, the status of the key recovery agent certificates is not loaded. When you click on apply, the service restarts and the status should be valid.
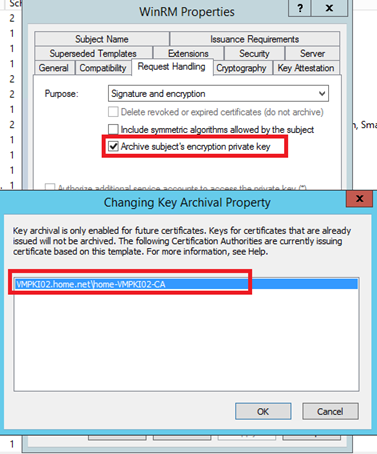
Now to archive the private key in the Key Archival, edit the template that you want and navigate to the Request Handling tab. Tick the Archive subject’s encryption private key checkbox. Select the Key archival and click ok:
Now, private keys will be archived to the Key Archival. To understand the user key recovery, I recommend you this topic.






